Protocol Based Intrusion Detection System Diagram
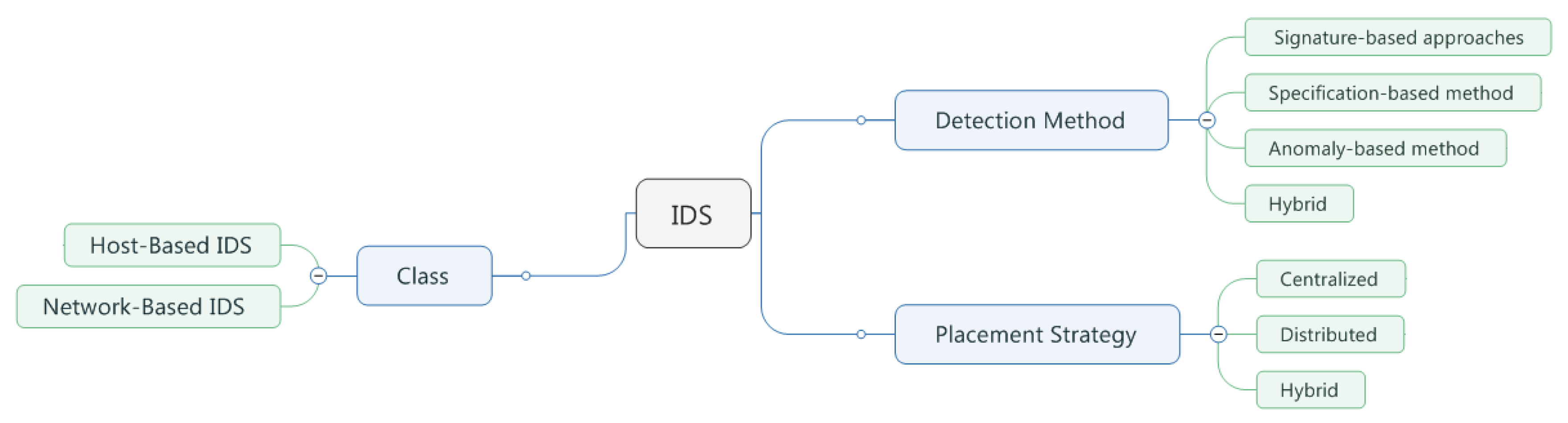
A network based intrusion detection system nids sniffs network traffic packets to detect intrusions and malicious attacks.
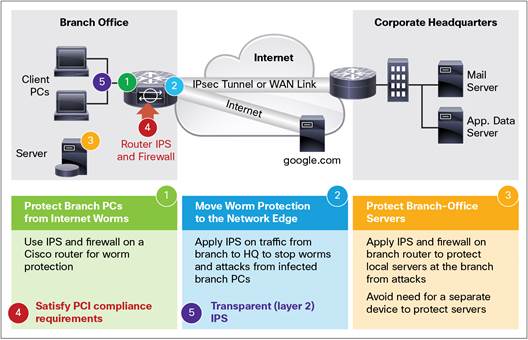
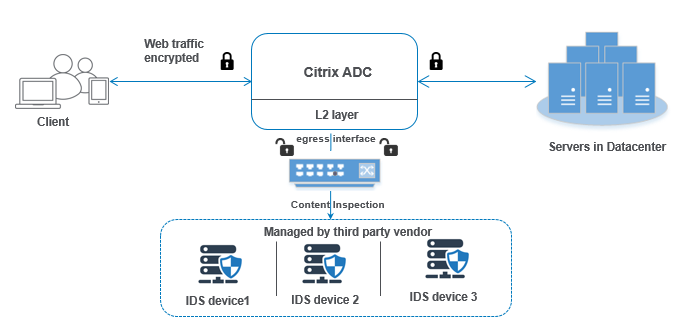
Protocol based intrusion detection system diagram. A protocol based intrusion detection system pids is an intrusion detection system which is typically installed on a web server and is used in the monitoring and analysis of the protocol in use by the computing system. What is inline mode. Intrusion prevention system ips host based intrusion detection systems. Nids can be hardware or software based systems and depending on the manufacturer of the system can attach to various network mediums such as ethernet fddi and others.
The pros and cons of this method are summarized in table 11 5. What is the mode of the ips from the diagram below. The life expectancy of a default installation of linux red hat 6 2 server is estimated to be less than 72 hours the fastest compromise happened in 15 minutes. Name few of the vendor who deals in ips ids.
Protocol based intrusion detection system pids comprises of a system or agent that would consistently resides at the front end of a server controlling and interpreting the protocol between a user device and the server. A nids can be either a software based system or a hardware based system. It is trying to secure the web server by regularly monitoring the https protocol stream and accept the related http protocol. What is promiscuous mode.
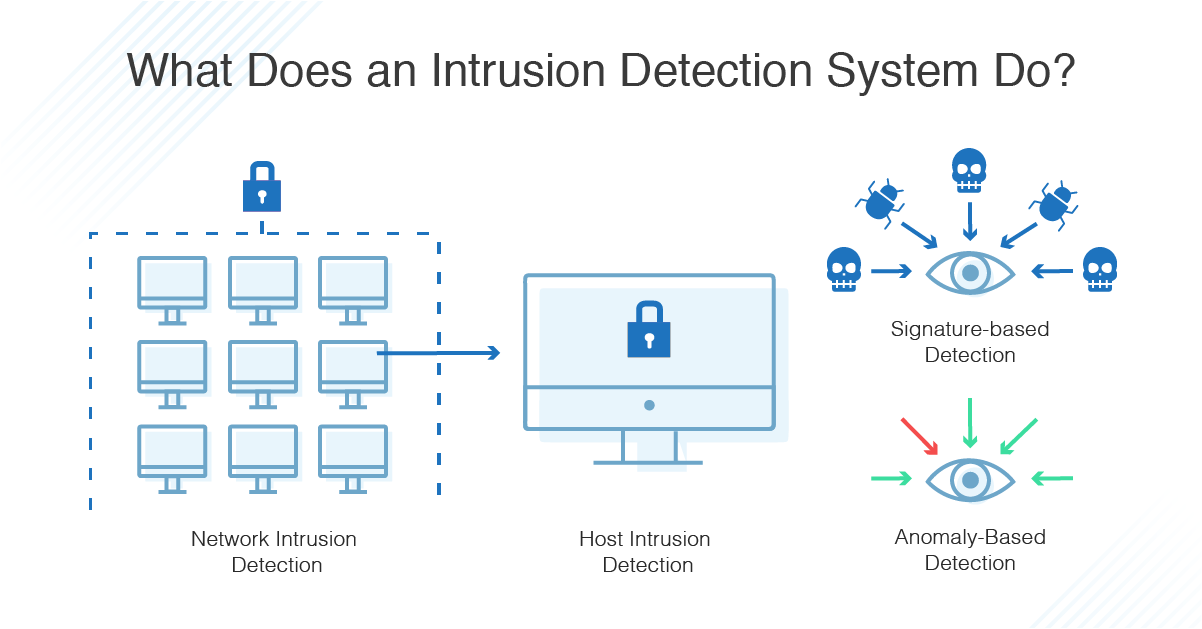
What is anomaly based detection. Network based intrusion detection systems nids are devices intelligently distributed within networks that passively inspect traffic traversing the devices on which they sit. Host based idss are designed to monitor detect and respond to activity and attacks on a given host. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management siem system.
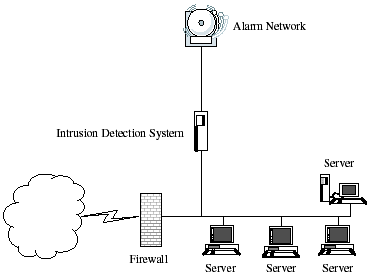
A pids will monitor the dynamic behavior and state of the protocol and will typically consist of a system or agent that would typically sit at the front end of a server. What are two modes of ips. A siem system combines outputs from multiple sources and uses alarm. An intrusion detection system ids is a device or software application that monitors a network or systems for malicious activity or policy violations.
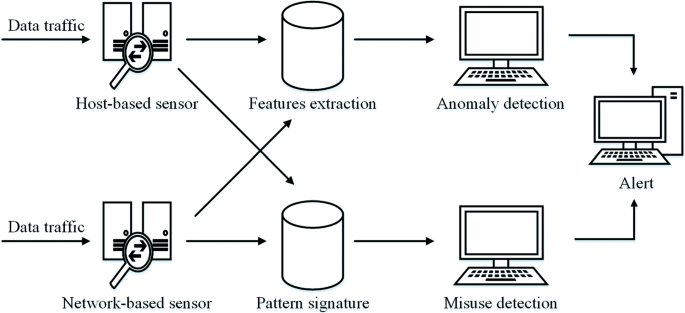
What is signature based detection. Intrusion detection systems can be grouped into the following categories. If the protocol implementation varies from operating system to operating system then idps may not perform well in detecting the intrusions. The operational structure of a nids and its location in the network are shown in fig.
For example snort nids is a software based nids. Stateful inspection resource intensive. Designing and deploying intrusion detection systems. Remote data exchange protocol xml based communications protocol between sensors and management apps encrypted using ssl event and transaction message entity bodies consist of xml documents.
Acceptable protocol behavior then it can pass through.